How to use it
Assessment of the Critical Supply Chains
Published 25 April 2023
Under the Biden administration, the US Departments of Commerce and Homeland Security have reviewed the US information and communication technology (ICT) supply chain to assess its structure and vulnerabilities. The assessment covers risk analysis of communications equipment, data storage, end-user devices, and critical software.
Here’s how to use the Assessment of the Critical Supply Chains Supporting the US Information and Communications Technology Industry.
Why is the assessment of critical supply chains important?
The ICT sector is of increasing importance to the global economy, and for the United States, represents a growing component of GDP and a source of highly paid domestic employment. As ICT products and systems are used across all parts of the economy, including to support critical infrastructure like power grids and telecommunications, economic and national security vulnerabilities are inherent in this sector. It is important to understand the composition of supply chains supporting the ICT sector and any potential bottlenecks or dependencies that could weaken or be exploited to disrupt or cripple it. This assessment is highly informative about the current state of critical US ICT supply chains, and the role the US Government can play in addressing these challenges.
What’s in the Assessment of Critical Supply Chains?
The Assessment of Critical Supply Chains includes the following seven principal sections, along with an introduction, explanation of methodology, and appendices with reference information:
- Overview of the ICT Industrial Base;
- Current State of ICT Manufacturing and Related Challenges;
- Current State of the ICT Software Sector and Related Risks;
- Current State of the ICT Workforce and Related Risks;
- Cross-Cutting Supply Chain Vulnerabilities Impacting the US ICT Industrial Base;
- External Risks to the ICT Industrial Base Supply Chain; and
- Recommendations to Strengthen ICT Supply Chain Resiliency.
Overview of the ICT Industrial Base
- The US ICT industrial base is highly specialized and depends on complex, global supply chains that are geographically concentrated. (p. 15)
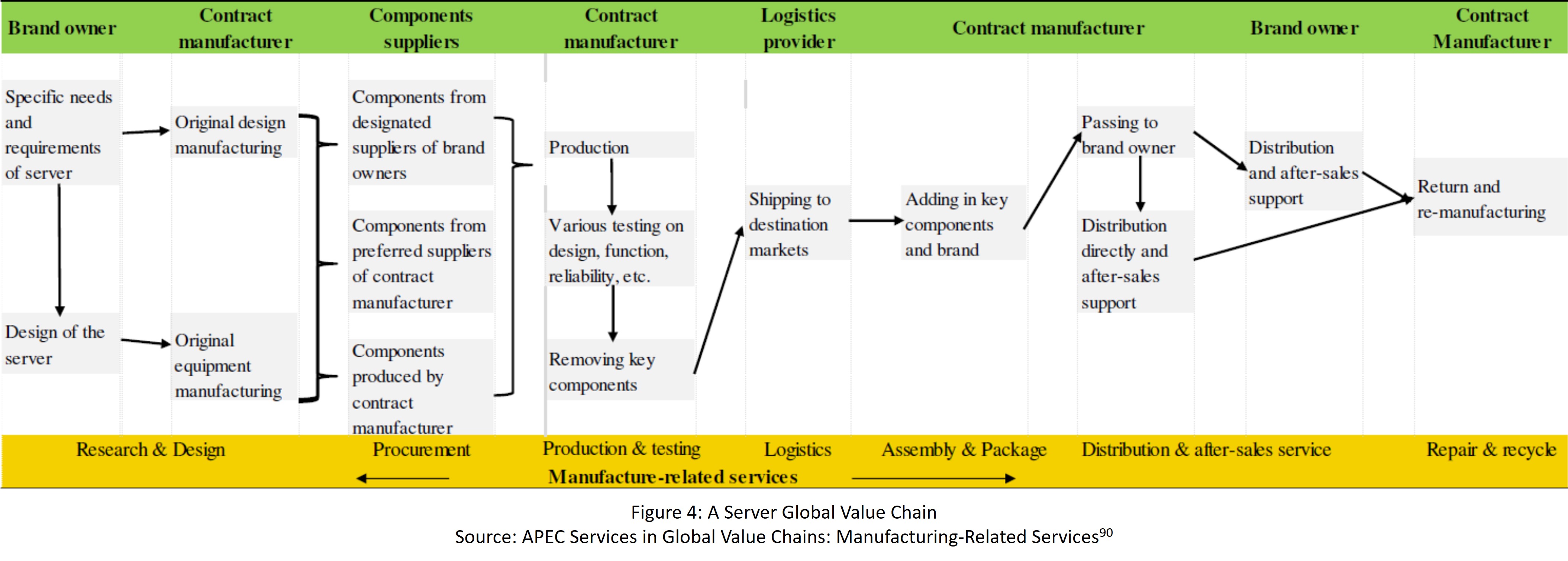
- The US ICT industry has shifted from being vertically integrated to highly outsourced, with the US leading in technology design and innovation, and China leading in manufacturing. (pp. 15-17)
- US companies stopped manufacturing because of low profit margins and the need for mass production to turn a profit; Asian economies, including China and Taiwan, offered lower labor costs, subsidies, infrastructure benefits, and the availability of capital and land. (pp. 16-17)
- Broadcasting and telecommunications equipment (communications equipment) is the backbone of the US critical communications infrastructure, which encompasses emergency services communications, air traffic control systems, and systems conducting financial transactions. (p. 18)
- Computing (computers, servers, and ATMs) and data storage products (hard disk drives and solid state drives) are vital to the US economy and are critical to many industrial sectors. (pp. 18-19)
- End-user devices (laptops, tablets, handsets, and displays) are ubiquitous across households, and necessary for virtual work and education, and for access to emergency services. (pp. 19-20)
Current State of ICT Manufacturing and Related Challenges: 5 Key Products
- Printed Circuit Boards (PCBs) are maps for the placement and interconnection of semiconductors, passive components, and electronic connectors, and are in all ICT hardware. (p. 21)
- Large-scale PCB manufacturing is concentrated in Asia, particularly China, Japan, Taiwan, and South Korea; US production is primarily low-volume, high-mix specialty boards. (p. 22)
- Key risks to the US PCB supply chain include 1) facility inefficiencies, as most facilities are older and dependent on manual rather than automated labor, lacking the ability to scale up production and the business case to attract investment for upgrades; and 2) heavy dependence on US defense contracts supplying PCBs for specialized use, which keeps them from developing economies of scale. (pp. 23-4)
- Fiber optic cable is composed of strands of glass that transmit large amounts of data using light beams, supporting international, national, and local communications. (p. 24)
- While the US maintains an industrial base, a large and growing share of fiber optic manufacturing takes place in Asia and increasingly China, which benefits from industrial subsidies. (p. 25)
- A key risk is China’s expected manufacturing capacity of 600 million kilometers per year by 2024, an amount that outstrips domestic demand by 300 million kilometers, leading to concerns over dumping that could put competitors out of business. (p. 26)
- PCB assemblies (PCAs) are semiconductors and other components placed on a PCB, which runs electronic functions in ICT and a broad range of goods. (p. 27)
- Most PCA assembly is done by Original Equipment Manufacturers (OEMs), Electronics Manufacturing Services (EMS) companies assemble 43% of all electronic goods globally, with China as the leading location for EMS production and most EMS companies headquartered in Taiwan. (p. 27)
- A key risk to the US supply chain is the use of counterfeit or used parts in PCAs or electronics, particularly those assembled in China given the high concentration of production there. (p. 28)
- Networking equipment, including routers, switches, and servers, is critical for transmitting data, distributing data processing, communicating across devices, and connecting networks. (p. 28)
- The US has several leading companies that supply networking equipment; most production is concentrated in Asia through EMS companies headquartered in Taiwan. (p. 29)
- Asia, in particular, leads in the final assembly of networking equipment manufacturing, with China developing an ecosystem through decades of target investments creating advantages for its capital, labor, and supplier and demand base, allowing for cost efficiencies, and faster product upgrades and customization; there is no significant capacity outside of China for key components of the networking hardware supply chain (p. 29)
- As demand for networking equipment increases and Chinese companies gain market share, there will be increased competition and price pressure for US companies. (p. 30)
- LCD displays are used extensively in the ICT sector and across many other industries, including healthcare and automotives. (p. 31)
- China is the largest producer of LCDs, followed by Taiwan, South Korea, and Japan; China’s LCD industry received government subsidies and tax breaks, allowing them to sell below cost, preventing cost-effective diversification outside of China. (p. 31)
- A key risk is supply chain consolidation in China, which relies on policies and pricing that renders firms outside of China unable to compete. (p. 32)
Current State of the ICT Software Sector and Related Risks
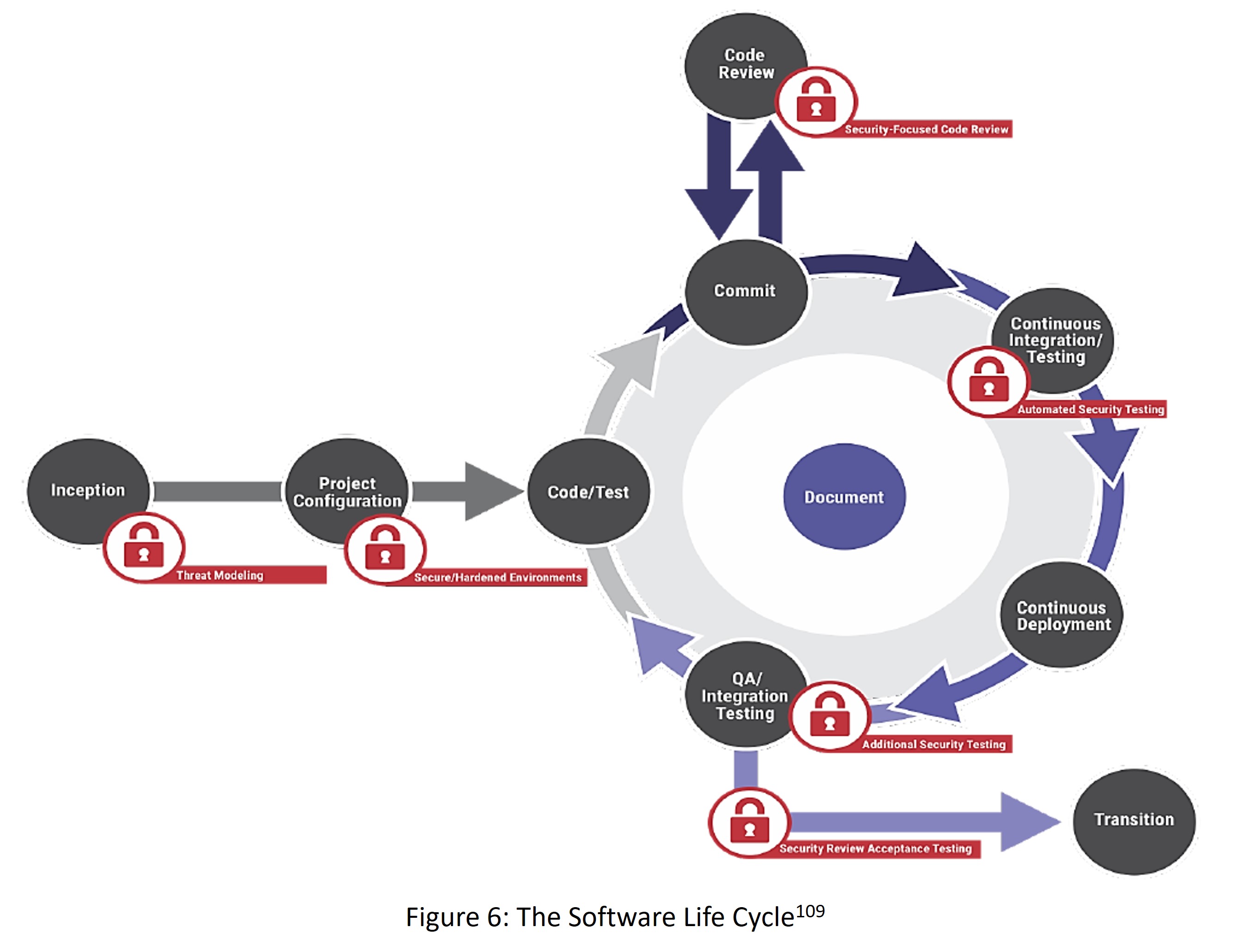
- A software supply chain is the entire sequence of events that impacts software from the point of origin to the point of end-use; every sequence affects the software and can strengthen it or introduce weaknesses. (p. 34)
- The US dominates the supply chain in terms of revenue and labor force; India is expected to overtake the US with the largest population of developers by 2024; Asia has the fastest growth rate for developers, ahead of Latin America. (p. 35)
- Open-source software (OSS) plays a critical role in software composition, with some components included in 75% of all code bases and comprising 70% of overall code; even well-known software and cybersecurity companies are among OSS users. (p. 36)
- OSS accelerates innovation and provides benefits, but can also introduce vulnerabilities, and lacks a single responsible entity to help organizations fix security issues. (p. 38)
- The use of software libraries allows for supply chain compromises, including package typo squatting, dependency confusion, and malicious injects. (p. 39)
- Firmware is a set of programs and data embedded into hardware and is crucial to system operation; it does not use code libraries and must be written from scratch. (p. 40)
- Firmware represents a single point of failure in devices that can be exploited through cyberattacks; attacks can bypass security systems, taking advantage of low-security barriers; complex supply chains can lead to confusion over who is responsible for maintaining integrity and supply customer updates; vulnerabilities may be compounded by update processes, which can vary widely or be non-existent. (pp. 41-43)
Current State of the ICT Workforce and Related Risks
- The US has approximately 274,000 ICT manufacturing-related jobs or around 5% of the domestic ICT workforce; about 54% are in semiconductor manufacturing; another 71,000 produce components like fiber optic cable and batteries; fiber optic production employment is expected to grow as demand increases. (pp. 44-45)
- 50% of employees are unskilled and require training when hired; 25% have some skills; 25% are in management (pp. 45-46)
- US PCB manufacturing suffers from a lack of qualified workers, driving outsourcing; component manufacturing relies on manual labor that can take years and large investments to train, leaving China dominant in this production; PCA factories require a wide range of skills and ongoing training. (pp. 46-47)
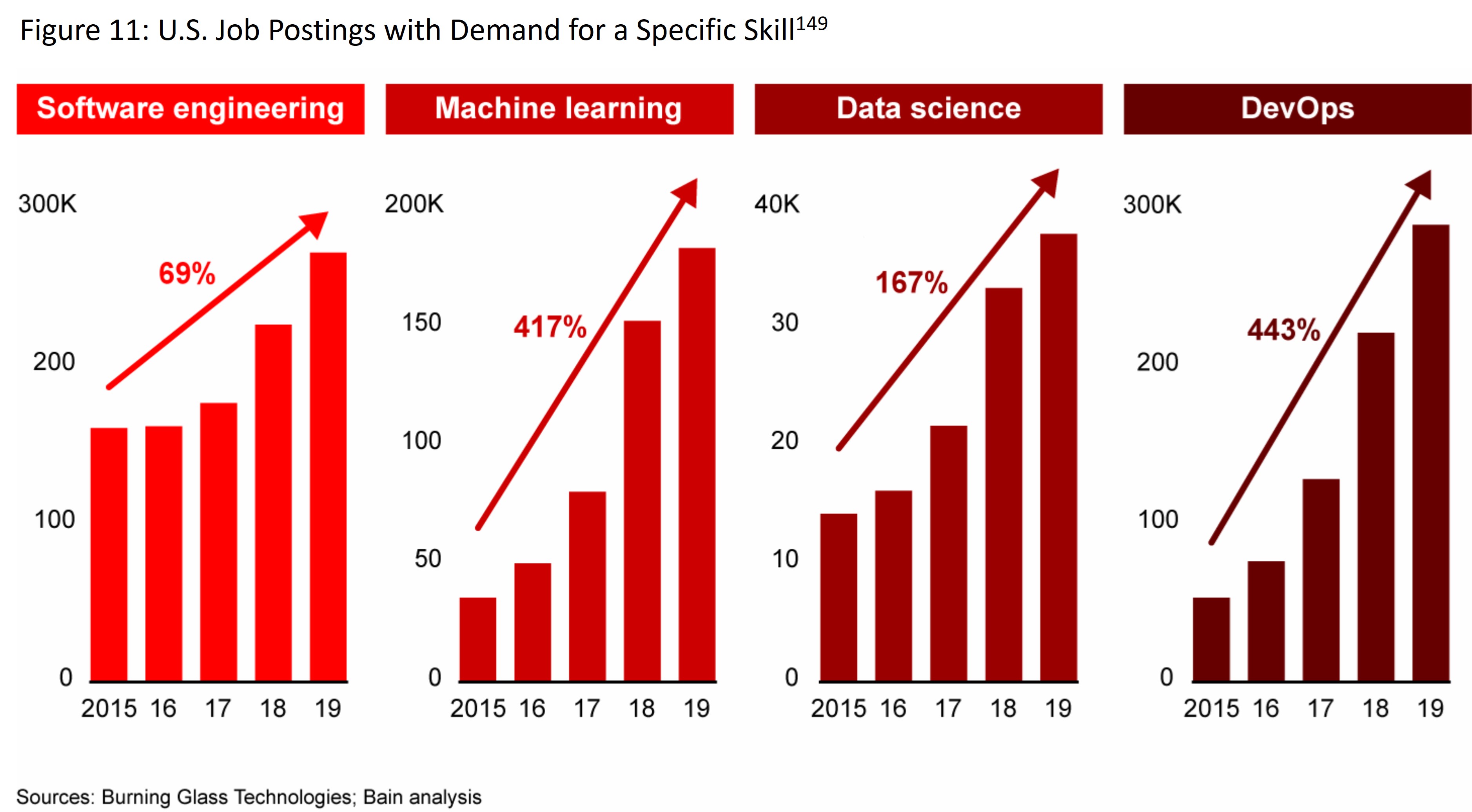
- The US software workforce accounts for 40% of domestic ICT employment and is a well-paid sector, characterized by intense and widespread competition for talent; demand for software developers is expected to increase in the US and globally in the coming years, from 24.5 million in 2021 to as much as 45 million in 2030. (pp. 47-49)
- A key risk is the lack of qualified workers, leaving a talent gap in the face of increasing demand; inadequate development of ICT-tracked educational and training programs, lack of inclusive access and awareness of training and opportunities, and limited capacity and development of broadband infrastructure contribute to the lack of qualified workers. (pp. 50-53)
How to apply the insights
-
This section provides a useful and brief guide to current employment and future employment trends in the ICT sector, with an explanation of the challenges to meeting demand in this sector.
-
This analysis should allow policymakers to focus on the key problems and find solutions to address them.
Cross-Cutting Supply Chain Vulnerabilities Impacting the US ICT Industrial Base
- The pandemic created sudden supply and demand shifts and bottlenecks, with dramatically increased demand for electronic devices and digital infrastructure occurring while pandemic-related work restrictions cut production, including of key components and inputs in the ICT supply chain; delays negatively affect US economic growth and activity. (pp. 54-55)
- The US lacks an ecosystem for electronics production compared to China, whose government-sponsored funding and policies created advantages in terms of capital, labor, and supplier and demand bases to create production efficiencies; China continues to be an attractive global manufacturing base; lack of geographic proximity to key components and high costs of capital and labor are barriers to the investment needed for geographic diversification. (pp. 55-57)
- ICT supply chains are long and complex, and products incorporate many components, some of which have only a single source or come from a single region due to limited options, unique qualities of a product, and need to control costs; lack of flexibility can have devastating consequences when the sole supplier cannot provide components; initiatives like O-RAN and diversifying production locations can mitigate this risk. (pp. 57-59)
- The complexity and size of ICT supply chains mean that companies lack visibility of their junior-tier suppliers which can introduce vulnerabilities into a supply chain and make it difficult to adopt strategies to provide redundancy and flexibility. (pp. 59-61)
- Increased competition and compressed profit margins have driven companies to adopt just-in-time inventory management, which relies on flawless production and execution, but breaks down during unexpected disruptions like natural disasters; firms are beginning to hold more inventory, a practice that favors larger firms but places SMEs at a disadvantage. (p. 62)
- ICT manufacturers and suppliers and every company, organization, or individual that uses ICT products, are part of a vast, global supply chain, which provides a large attack surface for anyone who wants to infiltrate it or cause harm; threats can include insider threats, vulnerabilities from extended supply chains, and dangers from counterfeit parts. (pp. 63-68)
How to apply the insights
- This section helpfully identifies the key vulnerabilities in the US ICT supply chain that can harm the US economy, including companies and individuals that rely on ICT products, and create vulnerabilities for national and economic security.
- These insights should help to focus policymakers on addressing these vulnerabilities and the working environment to fix supply chain challenges.
External Risks to the ICT Industrial Base Supply Chain
- Malicious cyber intrusions, including stealing intellectual property, corrode the development, utilization, and innovation of hardware and software applications throughout the ICT supply chain, while state-sponsored cyber intrusions threaten domestic industry and national security. (pp. 70-71)
- Economic risks stem from the offshoring of ICT manufacturing, which limits capital inflows to the US, inhibiting the development of a domestic ICT manufacturing sector that could bring greater innovation and employment in high-quality jobs. (pp. 71-72)
- The complexity and size of ICT manufacturing supply chains, and their location in developing countries, create a risk that forced labor could be used in parts of a supply chain and may be difficult to identify given limited information on secondary and tertiary suppliers. (pp. 73-74)
- The ICT supply chain’s extended length, with a high concentration in certain links of the chain, makes the ICT industry vulnerable to disruptions from climate-related events. (pp. 74-75)
Recommendations to Strengthen ICT Supply Chain Resiliency
- Revitalize the US ICT manufacturing base by supporting the private sector in expanding manufacturing capacity through financial incentives and procurement preference. (pp. 76-77)
- Build resilience through secure and transparent supply chains, including through promoting supply chain risk management practices through procurement and monitoring efforts. (pp. 77-78)
- Collaborate with international partners to improve supply chain security and resiliency, including by improving international collaboration to advance shared interests. (pp. 78-79)
- Invest in future ICT technologies by sustaining the R&D ecosystem through federal programs and legislation. (pp. 79-80)
- Strengthen the ICT workforce pipeline by supporting and expanding programs that attract, educate, and train the ICT workforce. (pp. 80-81)
- Ensure sustainability remains a cornerstone of ICT development by promoting environmental standards through financial incentives and government programs. (p. 81)
- Engage with industry stakeholders on resiliency efforts by strengthening public-private engagements; carry out a continued study of the ICT industrial base - guide long-term policy through further studies. (p. 82)
How to apply the insights
-
This section provides helpful and specific policy ideas for policymakers and lawmakers to use when developing a strategy for reviving and building resiliency in the ICT supply chain.
Conclusion
The Assessment of Critical Supply Chains is a useful resource for understanding the current state of the ICT industry globally and the role of US ICT companies in this industry, as well as the weaknesses, vulnerabilities, and threats to US economic and national security that are part of the current structure of the sector. US policymakers can use this report to understand challenges to the US supply chain and create new policies and laws to address those challenges. Readers in other economies can also apply this resource to evaluating their own interests, weaknesses, and vulnerabilities and gain ideas for how to develop their ICT sectors in the future.
Complementary reports and analysis
Hinrich Foundation
- Digital technology and global integration: Opportunities for innovative growth
- Global flows: The ties that bind in an interconnected world
- Solving the microchip shortage
External Resources
- The complication of concentration in global trade – McKinsey Global Institute (MGI)
This article builds on the findings of MGI’s recent research on global flows, analyzing concentration across more than 120 countries, roughly 6,000 products, and eight million individual trade corridors. - How Apple tied its fortunes to China – Financial Times
Patrick McGee offers a deep dive into how Apple decided to tie its fortunes to China. - Supply Chain Diversification in Asia: Quitting China Is Hard – Macro Polo
The electronics and machinery sector would be a useful proxy to examine supply chain shifts, as it is the largest category in global trade by value.
© The Hinrich Foundation. See our website Terms and conditions for our copyright and reprint policy. All statements of fact and the views, conclusions and recommendations expressed in this publication are the sole responsibility of the author(s).